
Red Team Service
Review your Cyber Defense
Red Team Service
Review your Cyber Defense
What is a Red Team?
In cyber security, Red Team refers to a group that assumes the role of an adversary or attacker and performs an assessment of the security status from this perspective. A Red Team Service is thus a hacking simulation aimed at assessing and training the organization's defenses to withstand a real attack.
Blue versus Red - Good versus Evil: The Blue Team in the organization is usually the SOC or Cyber Defense Team.
Scope
The scope of a Red Team service is always unique and is determined during the preparation phase of the engagement. It can include any resource that is under the control of the target organization:
- Technologies
- People
- Processes
The stages
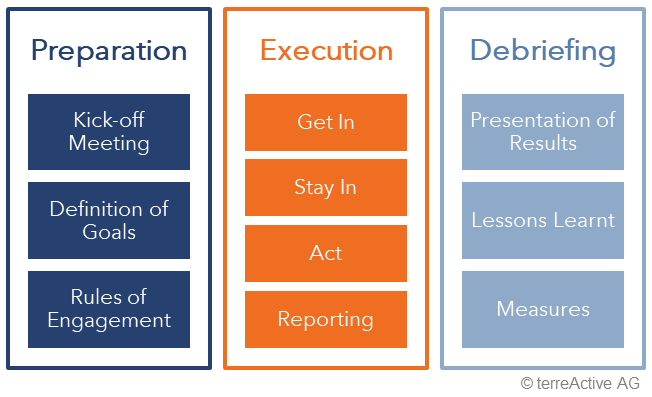
The kick-off meeting is an important part of the preparation stage, as it is here that the rules and objectives of the engagement are defined.
The execution stage consists of three substages, all results will be included in the report.

- Get in: The Red Team attempts to penetrate the network and gain a foothold in the company's infrastructure. This is done by using real hacking methods such as social engineeringor executing direct attacks on applications or services exposed to the Internet.
- Stay in: This is where the Red Team moves around the corporate network and strengthens its position within the infrastructure. By doing so, the team finds the best starting point for its attack on the desired target (personal data, account numbers, construction plans, etc.).
- Act: carrying out the operations that enable the Red Team to achieve its goals.
In the debriefing or even during a workshop, the results of the operation are presented to the company. The lessons learned are summarized and it is ensured that the recommendations to improve Cyber Defense are properly understood.
Customer profile: Who should use this service?
The Red Team Service is particularly suitable for medium and large companies that want to review and improve their cyber security defens. For a serious preparation, execution and subsequent analysis, we calculate at least 15 working days on the part of terreActive.
Differentiation: Do I need a penetration test or a red teaming?
Although they seem to be similar in terms of methodology, penetration testing and red teaming are very different with regards to their intentions:
- The goal of a pentest is to find as many vulnerabilities as possible, exploit them, and determine the level of risk associated with each vulnerability.
- A Red Team, on the other hand, is not trying to create a comprehensive list of all your organization's vulnerabilities. Here, the goal is to find an entry point, exploit it, and then move laterally through your system to access the most interesting data. The main goal of the Red Team service is to find out if and how quickly your internal IT detects the attack. And finally to assess those defense measures that are already in place. defenses.
Findings and improvement actions from Red Teaming thus strengthen and increase your cyber defense in the long run.
What the CISO wants to know: Red Team versus Blue Team
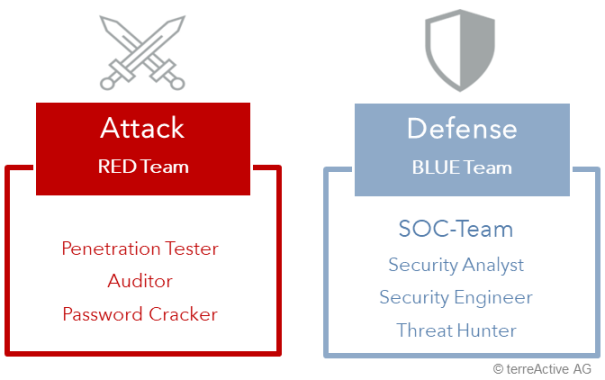
The Red Team must do everything possible to avoid being detected by the Blue Team.
The CISO wants to know at what stage (cyber kill chain) the Blue Team detects the attack, what technique the attacker uses, and what tools the Blue Team used to detect the attack. And of course, how and how quickly the Blue Team can react and take action. If the attack remains undetected, the CISO must figure out what tools are needed by his Blue Team to be more successful in the future.
As one of the few security providers in Switzerland, terreActive has both a Red and a Blue Team. From the «fight» of the teams we draw valuable insights for our own defense and that of our customers. Each team is forced to use the latest techniques if it wants to win, to optimize its processes for speed and to continuously expand its know-how.
