
Social Engineering
Phishing and Awareness
Social Engineering
Phishing and Awareness
Phishing as part of cyber security
A phishing campaign complements the security audit and gives an insight into the company's security. It can be carried out independently as a quick introduction to cyber security or as part of a complete audit project. Awareness for social engineering is a continuous process that must be constantly repeated, varied and improved. Phishing attacks have increased dramatically and are trending upward. Protect yourself from phishing attacks!
What is phishing?
Phishing is an inexpensive gateway for cybercriminals to enter the corporate network or spy on sensitive data. The attacker uses e-mails or fraudulent websites to try to obtain information such as access data or to plant malware. As a supposedly trustworthy counterpart, the attacker exploits the victim's credulity: perfidious tricks are used to encourage the victim to enter sensitive information in false domains (typosquatting) or to download malicious files. Phishing is one type of social engineering and is very popular as cyberattack, as criminals can make big money with little effort. The likelihood that employees will fall for the scam is very high; humans are the weakest link in the security chain.
The best protection is trained employees who know the threat scenarios and pay attention to IT security in their daily work.
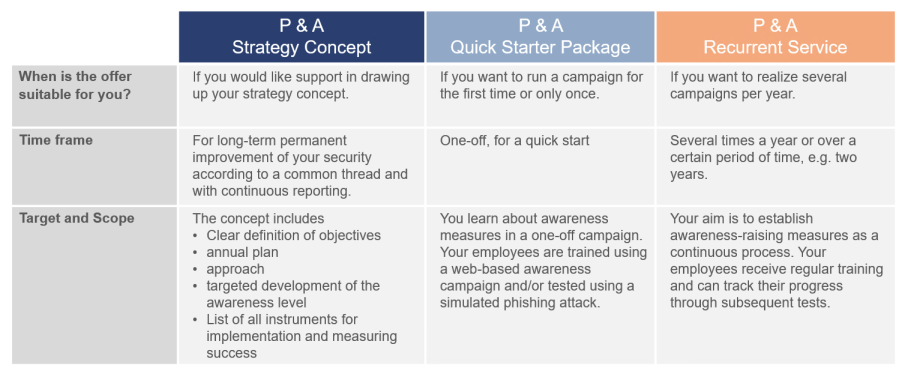
Protect yourself: phishing and awareness offer
terreActive offers support regarding concept for your phishing and awareness strategy or for the implementation of campaigns ̶ whether this is a one-time activity or a recurring service. A selection from our range of services:
You want another model? Let us advise you without obligation, here you can get to know our sales team.
Benefit: Why phishing prevention pays off for you.
Today, investments in technical protection measures alone are no longer enough.
Phishing simulation and awareness campaign bring benefits to your company:
- The awareness level of employees is determined and shows where there is potential for improvement.
- Trained employees provide valuable protection against cyber attacks as a human firewall.
- This means that a cyber attack can be detected early - costly malware attacks are prevented.
- You can avoid image damage and bad press for your company.
- Security guidelines support employees in the correct behavior in the event of social engineering.
- Collaboration between employees and the service desk shows where processes should be optimized.
- Further insights into the potential for improvement on a technical or software-based level.
Experience brings efficiency - process of a project
Reduce your own effort. You will achieve results faster if you take advantage of terreActive's experience from numerous social engineering projects. With our security know-how, we execute your campaign in a technically professional manner. With the subsequent report you can inform different target groups and eliminate detected security vulnerabilities. Ask for our references.
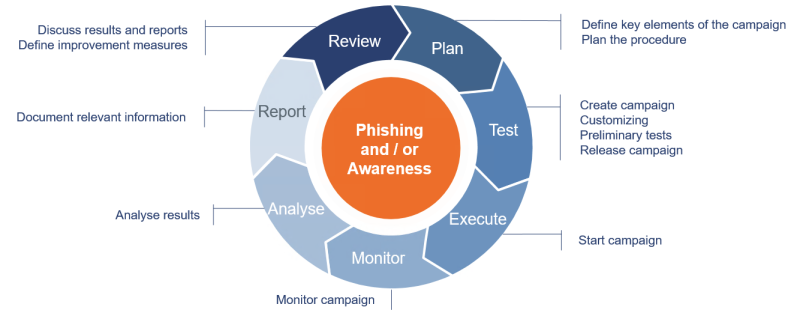
With a professional phishing prevention, you continuously increase your protection and thus increase the cyber defense of your company.


